 This image has not been stegged.
This image has not been stegged. |
 This image has been stegged using Camouflage. Password: test
This image has been stegged using Camouflage. Password: test |
There are a half dozen programs used to hide files in images. This tutorial will focus on Jphide and Camouflage. The major drawback to using steganography in Alternate Reality Games is that only users of Windows have the ability to desteg them. This is not a Mac-friendly puzzle technique.
Camouflage
To download Camouflage freeware go to http://camouflage.unfiction.com/
When you encounter an image you believe to contain a hidden file, right click on it and save the image to your hard drive. Note: You must use the image in its original condition to properly recover the hidden file. Stegged images that have been altered for size or shape may be corrupted.
 This image has not been stegged.
This image has not been stegged. |
 This image has been stegged using Camouflage. Password: test
This image has been stegged using Camouflage. Password: test |
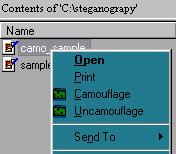 |
After Camouflage is installed this is what it looks like when you right click on the image file in Windows Explorer. Choose Uncomouflage. |
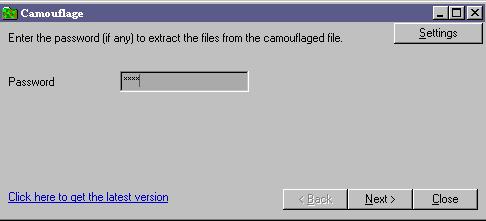 |
This is the first window that opens when you click uncamouflage. Enter your password attempts. |
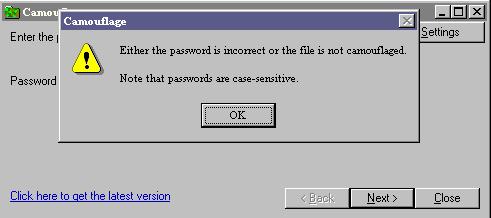 |
If your password fails this is the error message you will receive. Click OK and try again. |
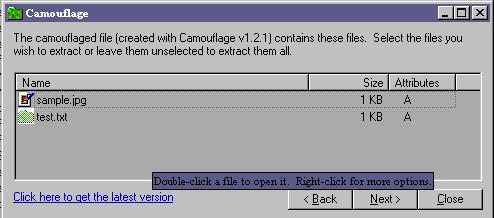 |
If your password succeeds then this window will open and you can click on the file or files to open. |
Hint: Not all files are what they appear to be. Sometimes
a destegged file must be renamed with a different file extension such as
.doc to discover what it truly is.
To download jphide/jpfind freeware go to: http://www.webattack.com/get/jphide.shtml
 This image has not been stegged.
This image has not been stegged. |
 This image has been stegged using jphide. Pass phrase: password.
This image has been stegged using jphide. Pass phrase: password. |
When you encounter an image you believe to contain a hidden file, right click on it and save the image to your hard drive. Note: You must use the image in its original condition to properly recover the hidden file. Stegged images that have been altered for size or shape may be corrupted.
Launch Jphswin and click Open jpeg. Select the image file you wish to desteg.
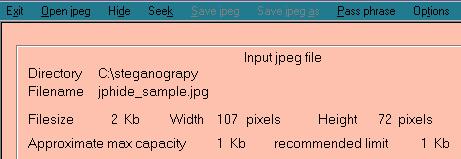 |
This is what it looks like when you select a file. |
Select Seek. You will be prompted for a pass phrase.
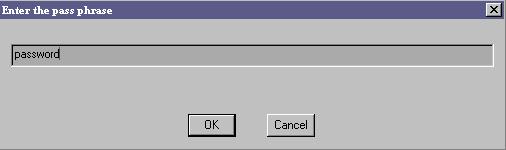
You will be prompted to save the file. You must give the file a different name than the file being destegged. Again, you might have to try different file extensions to get the right one.
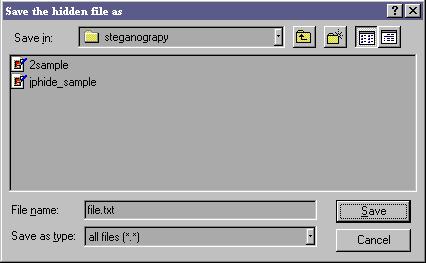
Now go to Windows Explorer and click on the new file just created. Providing the right file extension was chosen then the hidden file should open properly. If not, try again with a new one.
I have no knowledge of how to use Stegdetect. Some swear by its results, others are continually frustrated by the numerous false positives or the difficulties encountered in accurately interpreting the results. It has been my experience that if PMs want players to desteg an image that it is generally fairly obvious.
http://members.tripod.com/steganography/stego/software.html
Return to tutorial home.